apk逆向__他趣APP脱壳&运行环境检测分析
ROOT检测
“ 当前APP运行环境存在风险 (Root设备),请您及时知晓并注意信息安全! “
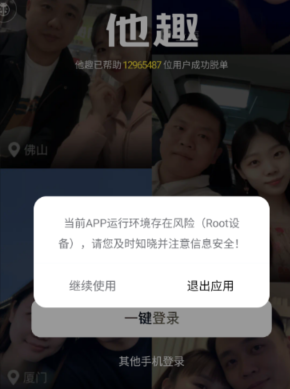
Hook 检测
使用算法助手定位到root检测弹窗的一些常规设置,去除弹窗,或者其他的绕过。
当使用算法助手hook app 的时候,app 会检测hook 的环境,从而闪退。
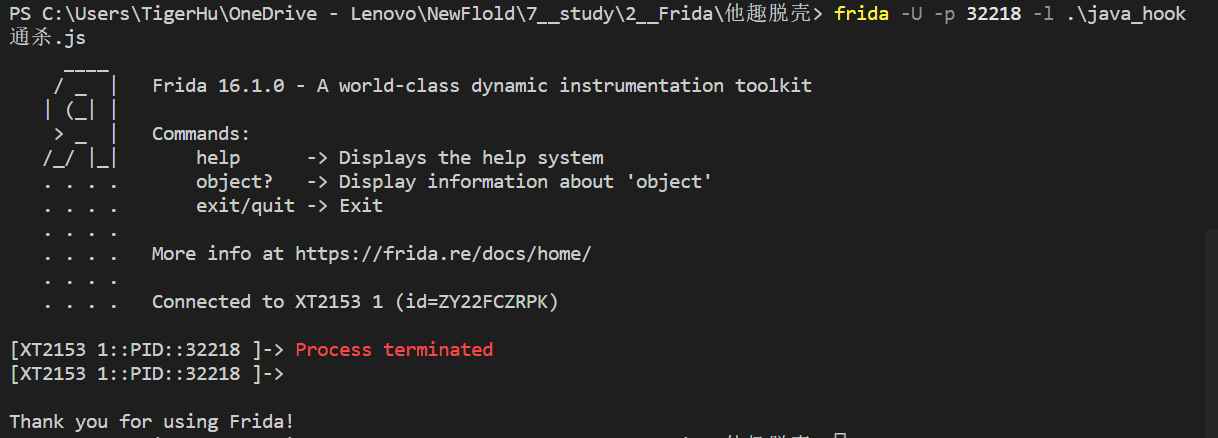
使用frida 脚本直接闪退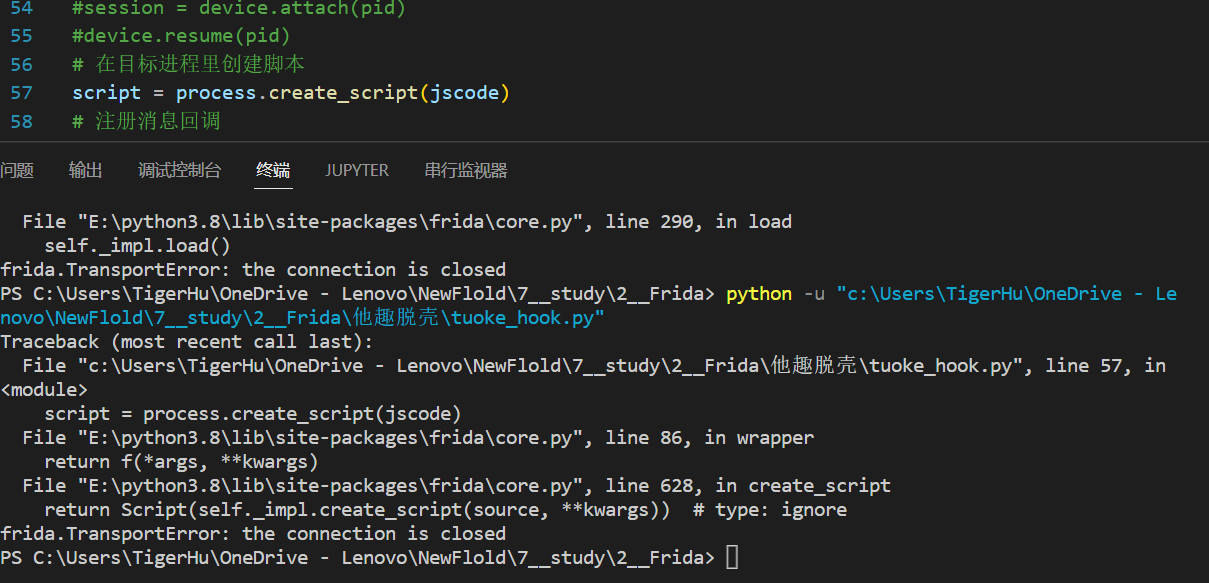
frida -U -p 32218 -l .\java_hook通杀.js
可以看到直接会闪退。
load_so.js
这里可以判定apk 使用了一些方法来阻止frida 进行hook, 一般是在 so 文件内进行处理。所以这里我们直接可以找找app在运行的过程中,使用了那些so。最后调用的那个so 文件,就是检测hook环境的库文件。
1 | |
使用脚本一直不行,因为用的一直是attach模式
1 | |
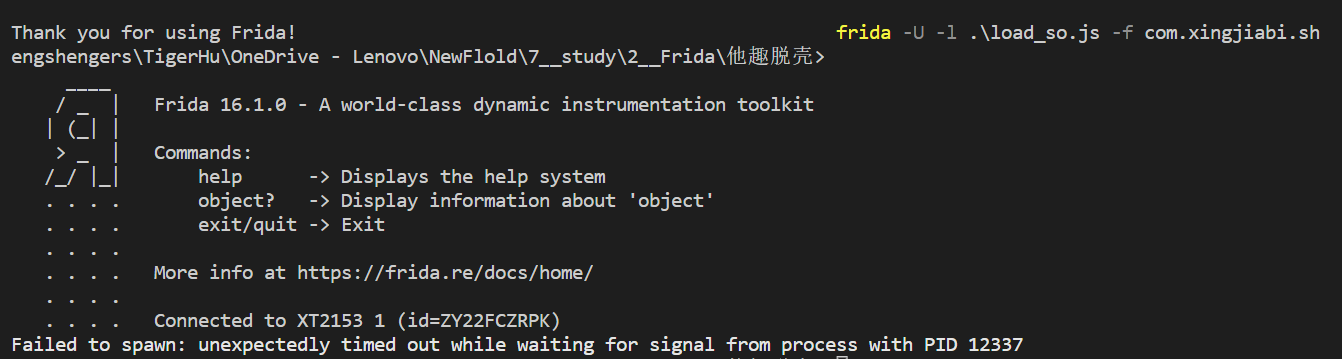
使用 spawn 模式,可以看到是 libnesec.so 文件,这是网易易盾的加壳so。
这是pixel 6Pro 手机hook ,可以看到。
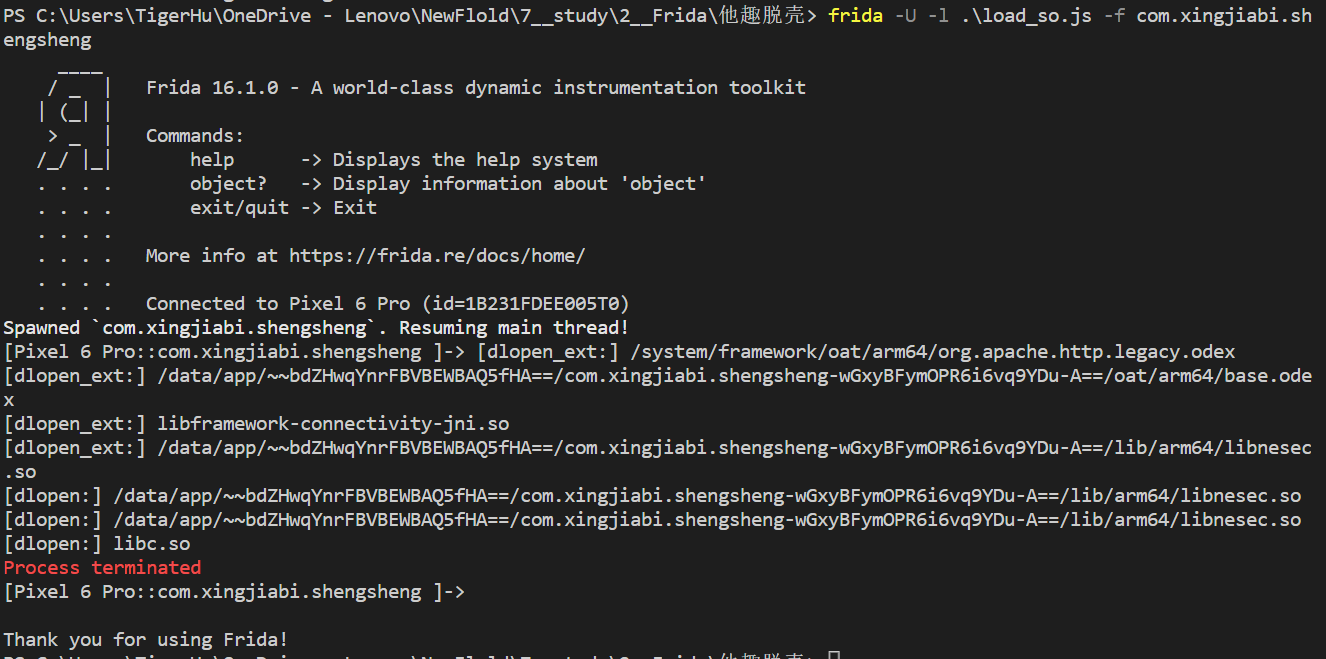
但是换成moto 手机却不行,“ Failed to spawn: unexpectedly timed out while waiting for signal from process with PID 12337 ”,猜测这与手机系统有关。
hook libnesc.so
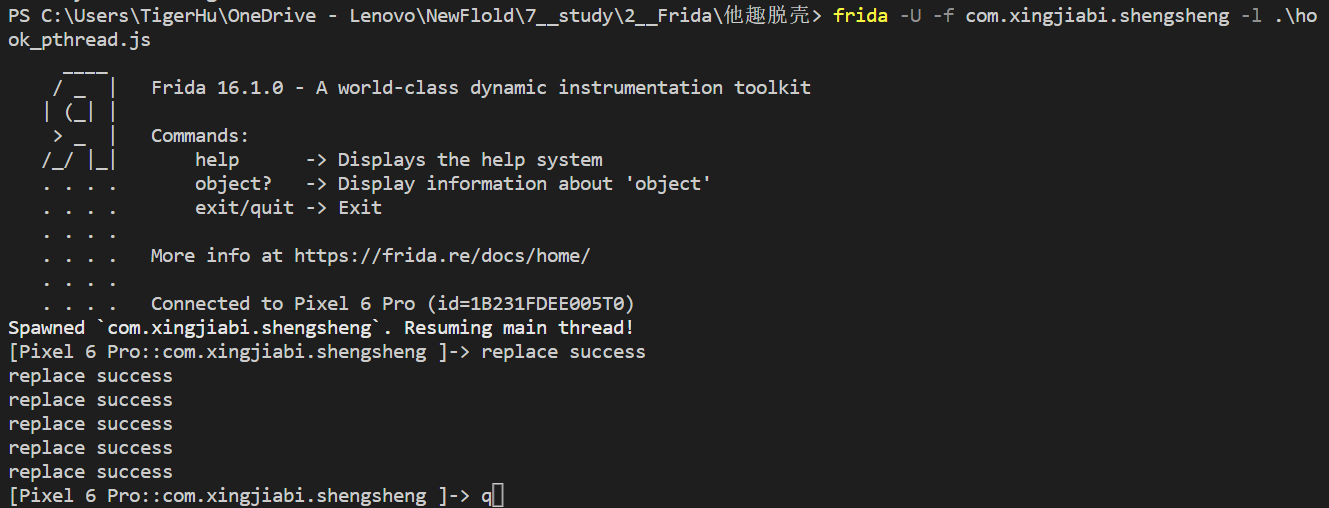
前面我们知道 libnesec 会检测frida hook, 那么可以直接hook libnesec.so ,当调用libnesec 库的时候,让其返回空
1 | |
可以看到替换成功了。
网易易盾脱壳
使用 jadx 打开 apk ,会发现存在 libnesec.so 文件,猜测加固了。因为反编译看不到要的伪java源码。因此需要去脱壳。
查壳
MT 管理器
可以查出来是网易易盾的加固
PKID 查壳
查不出来,看过别人用pkid 可以查出来,可能版本不一样。
dump_dex脱壳
脱壳前提: 要一直运行hook_libnesec.js 文件,保证frida 能够hook 而不被libnesec.so 检测到闪退,影响脱壳。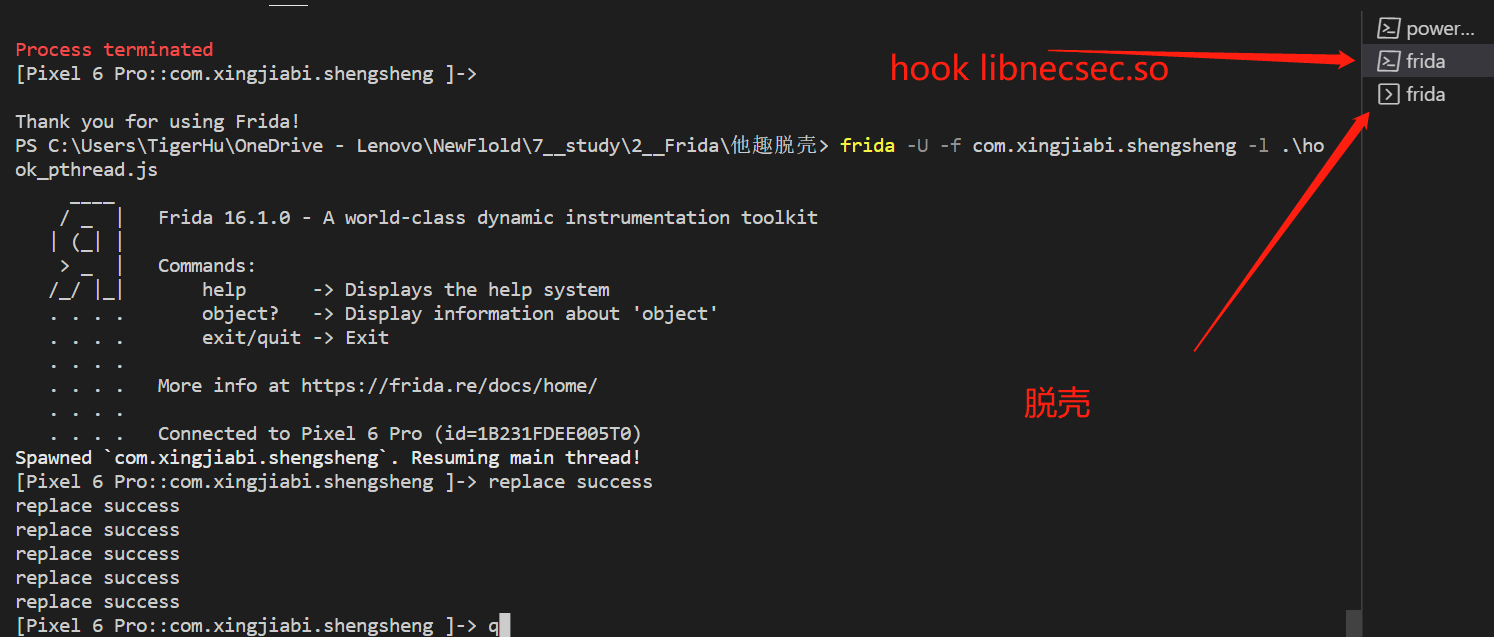
脱壳脚本
1 | |
运行 frida -UF -l .\dump_dex.js , 为了保证能脱壳,app 的每个板块都点一点。
1 | |
在手机内可以看到脱壳出来的dex 文件,随后直接拖到jadx里,就可以分析了。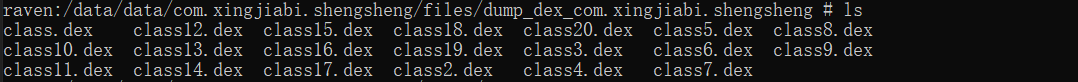
分析app内各种检测
分析app 反调试、运行环境检测技术。
root 检测
前面我们知道app 会对运行环境进行检测,但是直接搜索 字符串 弹窗的信息,是搜不出来的,这是由于 apk 对字符串做了base64 处理。
然后以前分析过一些对root 环境监测的代码,所以这里直接搜索,定位到代码 cn.taqu.lib.base.utils.AppAntiUtils.isDeviceRooted()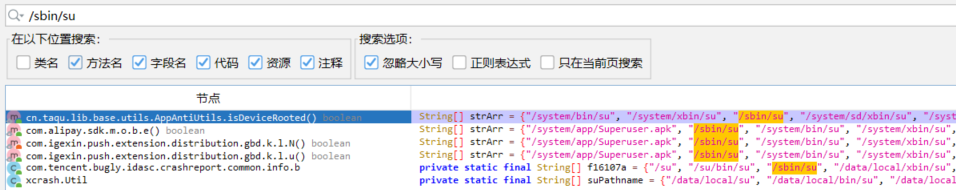
然后找到这一块的代码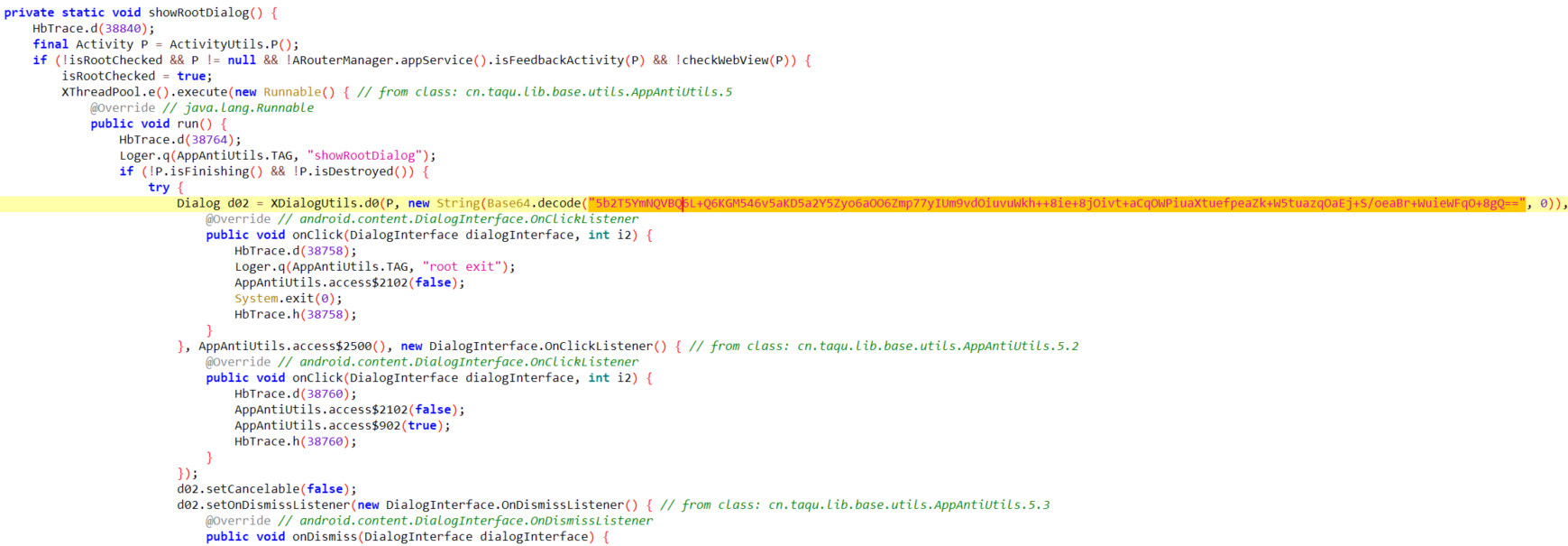
base64 解码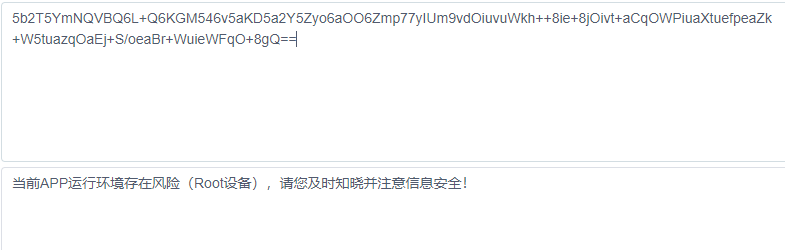
另外还看到不仅仅对 su 进行检测,还检测了其他的项,如下函数。这个函数在 cn.taqu.lib.base.utils.AppAntiUtils.initAnti() 初始化的时候调用,
1 | |
可以看到调用了 isDeviceRooted,两个重构函数,来判断是否root,最后弹窗
1 | |
这里来分析一下 isDeviceRooted(RootBeer rootBeer) 内对运行环境是如何检测的代码。
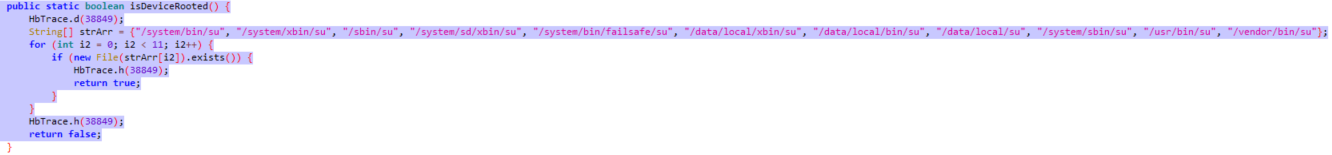
首先分析一下 rootBeer.checkForBinary(x.f13157a),这个函数是检测在一些文件路径内是否存在 x.f13157a ( su 文件 ), 有关Const.getPaths() 函数的代码详见附录 1 。
1 | |
rootBeer.checkForDangerousProps() 就是判断系统的调试模式是否被打开。
1 | |
rootBeer.checkForRWPaths() 检查系统中是否存在被挂载为可读写(rw)权限的应用程序数据目录以及其他指定的路径,并返回一个布尔值表示是否存在这样的路径。该函数会读取系统中关于挂载点的信息,检查每一个挂载点的路径和权限信息,如果发现某个路径被挂载为可读写权限,则会输出相应的日志信息并将返回值设为 true。该函数可以用于检测系统安全性,防止应用程序滥用高权限目录,代码太长,详见 附录 2 。
rootBeer.detectTestKeys() 该函数会读取设备的 Build.TAGS 字段是否有 “ test-keys ”,检测当前设备是否使用测试用的密钥签名。
root.Beer. checkSuExists() 函数会调用 which 命令,查找是否存在 su 命令。
rootBeer.checkForRootNative() 函数会加载本地 toolChecker 的 lib 库文件来检测是否被获取root 权限,调用 native 内的 checkForRoot() 函数,来判断设备是否获得root权限,其实还是检测是否存在 su 文件。
1 | |
rootBeer.checkForMagiskBinary() 检测是否存在Magisk 面具,如果进程名被更改就检测不到了。
1 | |
其实还有一些检测的代码,这个app 对root 检测已经是相当的全面了。
完整性签名校验
计算签名摘要,进行对比。
1 | |
代理检测
1 | |
参考
APP 使用frida 反调试检测绕过
https://www.cnblogs.com/dxmao/articles/17678351.html
附录
附录 1
1 | |
附录2
1 | |